7 Ways Compliance Will Bankrupt You in Australia (If You Don’t Act Now)
Stop pretending compliance is a tick-box. It’s your trust engine — and if you don’t make it work, you’ll lose contracts, customers and sleep. Hard.
(Read this first — then act)
Read the whole thing if you run a business in Australia — or at least copy the 30-day sprint and the 10-minute checklist on page two. Now, let’s get angry and get practical.

- Data breaches in Australia are rising and spectacularly expensive; they destroy reputations and invite regulator action. IBM+2OAIC+2
- Big breaches prove it’s not “if” but when for most organisations — and the OAIC and APRA are increasingly aggressive about consequences. OAIC+1
- The good news: practical, sprintable steps can cut your risk fast. This article gives plain-English plays, a 30-day sprint, interactive role actions, and real-world Aussie proof points with sources.
What most Aussie owners still don’t get
Imagine waking to an email from your insurer or regulator: “We’ve opened an investigation.” That email ruins weeks — maybe years — of hard work. It also kills tenders, eats legal costs, and turns customers into critics overnight.

Australia’s recent, high-profile breaches (big names you’ve heard of) show one thing: you don’t need to be massive to be destroyed. Your clinic, construction firm, accounting practice or marketing agency is at risk if your people, processes, and tech aren’t aligned for compliance.
Let’s be frank: people will call this “security theatre” until it happens to them. Don’t be “them.”
The cold, ugly data (so you stop rationalising)
7 Savage Compliance Truths (and what to do about each)
Below are the blunt realities — and tactical actions that actually move the needle.

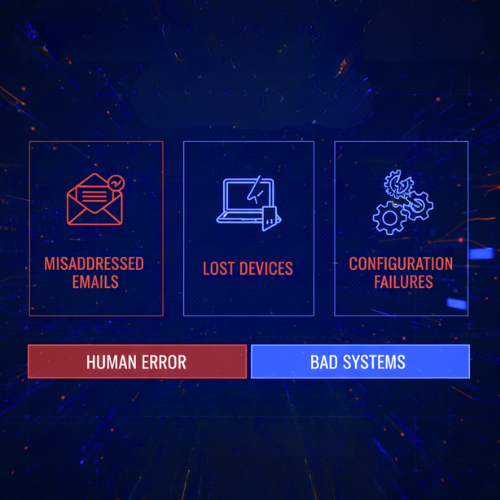
Truth: Most breaches are won by exploiting human error and poor processes
Phishing, misdirected emails, missing labels, lost USBs — these are the simplest paths for attackers. Technology helps, but if your people don’t follow basic handling rules, you’re still cooked.
Do this now: enforce MFA, run phishing simulation training quarterly, and implement mandatory sensitivity labels on data at creation. Turn on email safeguards that block emails to external domains unless specifically approved.
Evidence: OAIC reporting shows misdirected emails and cyber incidents remain top causes of breaches.
Truth: Big breaches aren’t rare — they trigger regulator action and public fallout
Medibank and other high-profile incidents have proven the OAIC will investigate and escalate; litigation and civil penalty proceedings are now public and painful. If your security posture is weak, you’ll be judged by the same standards — and public confidence evaporates fast.
Do this now: document every security control. If you claim “we encrypt backups” or “we backup daily,” create evidence: logs, retention schedules, and test results.

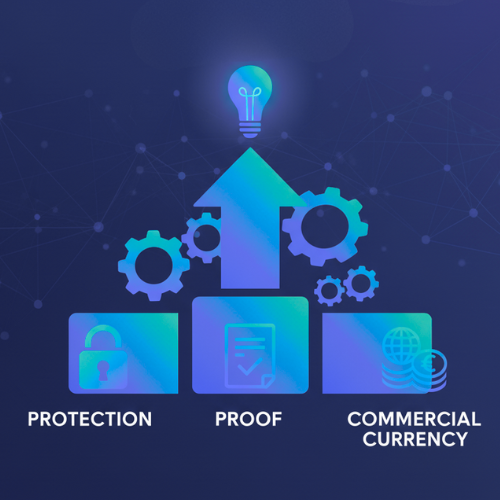
Truth: Standards aren’t bureaucracy — they’re protection, proof, and commercial currency
Tenders and enterprise partners increasingly demand proof of controls (ISO 27001, APRA CPS 234 alignment, Privacy Act compliance). If you can’t prove it, you won’t win big contracts.
Do this now: start an ISO roadmap in sprints (10 sprints strategy below). If you’re APRA-regulated, CPS 234 isn’t optional — it’s a duty.
Truth: Shadow AI and unapproved tools are the new leak vector
These aren’t theoretical risks. The OAIC explicitly warns against entering personal or sensitive information into public generative AI tools—doing so carries “significant and complex privacy risks.”
Do this now: publish an Approved AI Tools list, block known public LLM endpoints at the network level where practical, and log prompt inputs centrally for review.


Truth: Backups alone are worthless without recovery tests and drill discipline
Many firms have backups. Few have tested recovery within business timelines. Worse: backups sometimes include sensitive data retained without a proper legal basis.
Do this now: schedule quarterly recovery tests with actual RTO/RPO checklists. Harden backup media by encryption, and segregate it from primary environment access.
Truth: Your Incident Response Plan Is Worthless Without Practice
If nobody knows the drill, a breach becomes a three-ring circus: PR, legal, compliance, IT all flail and send mixed messages — and your regulator sees that as negligence.
Do this now: build an incident runbook with RACI, and run a table-top every quarter. Test real scenarios (phish→credential theft→exfiltration) and measure response times.

6 Smart Plays Aussie Companies Can Steal
(If You’re Slow, They’ll Rip You Apart)
These are no fluff; real plays you can start this week.
Aussie case studies (real, verified, and sobering)
Use these to frame the risk; they are public, sourced, and instructive.

Millions of personal and health claims were exposed; OAIC launched civil penalty action, showing sharp teeth. A national cautionary tale that every Australian business owner should fear and never forget.

OAIC began proceedings over systemic failures post-cyberattack; the case proves how health sector gaps in basic controls can quickly spiral into a Federal Court showdown with lasting consequences.

OAIC’s Notifiable Data Breach reports highlight root causes and rising volume — a steady drumbeat proving that human error mixed with poor controls makes breaches an unavoidable and costly certainty.
Important transparency note: some of the earlier hypothetical anecdotes (clinic with unencrypted USBs, builder losing tender) are dramatized composites built from sector trends and typical outcomes. Where we cite a specific case, we use public records and OAIC statements. When we create a stylised example, we state it clearly — credibility matters.
The 30-Day Smart Compliance Sprint
(do this even if you’re “too small”)
This is a battle-tested, practical sprint you can run with a lean team.
Week 1
Baseline & Executive Buy-In
- Executive briefing: 45 minutes — present simple risk heatmap.
- Inventory: critical systems, data types, vendor list.
- One-page core policies: retention, acceptable AI use, and incident response.
Week 2
Controls That Move The Needle
- Enforce MFA (every account, no exceptions).
- Turn on encryption for data-at-rest and backups.
- Implement sensitivity labels and mandatory metadata on new documents.
Week 3
Governance & Proof
- Create or update the risk register and map to controls.
- Conduct a Privacy Act gap check (health/finance gets extra scrutiny).
- Draft supplier risk addendums and ensure BAAs or equivalent are signed.
Week 4
Test & Publish
- Run a 2-hour incident simulation (phish → exfiltration).
- Publish a short internal “lessons learned” and update the runbook.
- Produce a one-page audit pack you could give a regulator or client.
Deliverables at day 30: MFA evidence, a labelled dataset sample, a test incident report, a supplier list with BAAs, and a 1-page compliance snapshot you can show clients.
10-Minute Audit-Readiness Checklist (print and pin this)

FAQ — Straight answers to the annoying questions
How SharePointPro helps (practical, no fluff)
You can do a lot internally, but modern compliance needs systems that automate evidence, reduce human error, and scale.
SharePointPro helps you:

Automate labels & retention so “where’s that file?” is answered in 2 clicks.
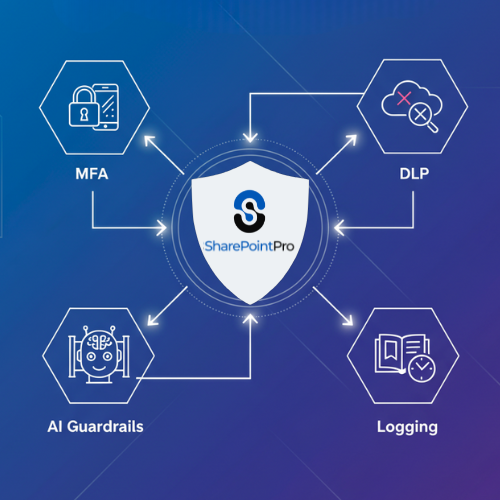
Enforce controls centrally (MFA, DLP, AI guardrails, logging).
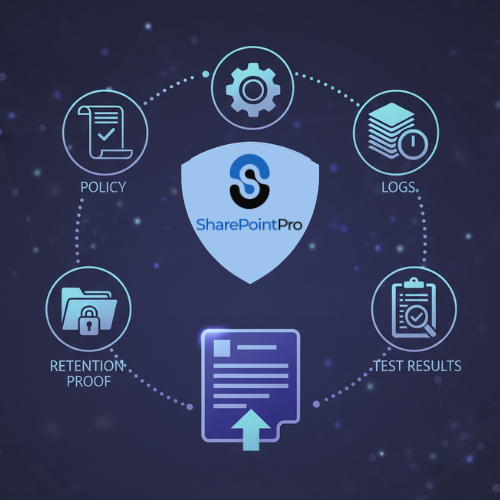
Produce an audit pack automatically: policy, logs, retention proof, and test results.
Simulate breaches and deliver after-action reports to clients or regulators.
If you want the “free” version — follow the 30-day sprint and the checklist. If you want the “done for you” version, SharePointPro builds the stack and hands you the evidence.
Final words (honest, no sugar)
Compliance is boring until it isn’t — and when it isn’t, it ruins businesses. The days of “we’ll deal with it if it happens” are over. Regulators, partners and customers now expect demonstrable control. If you want to win tenders, keep clients and sleep at night, treat compliance like product — make it part of your value proposition, not a cost center.
You now have:
- The ugly truth backed by sources. IBM+2OAIC+2
- A 30-day sprint to jumpstart change.
- Tactical plays and interactive role actions.
- A short checklist to become audit-ready fast.